Invisible PDF Tracking Exposed: The Hidden Surveillance
🕵️ The Invisible Threat
Right now, as you read this, countless PDF documents across the internet are silently watching, recording, and reporting on everyone who opens them. This isn't paranoia – it's the new reality of digital surveillance. Every click, every view, every second you spend reading is being meticulously tracked by invisible systems you never knew existed.
👁️ The Scope of Invisible Surveillance
📊 What's Being Secretly Monitored
- Your Exact Location - Pinpointed through IP geolocation
- Reading Patterns - How long you spend on each page
- Device Fingerprinting - Unique identification of your hardware
- Network Analysis - Your ISP, connection type, and security setup
- Behavioral Profiling - Psychological analysis of your reading habits
- Social Mapping - Who you share documents with
- Time Correlation - When you're most active and vulnerable
🔬 The Invisible Tracking Arsenal
👻 Ghost Pixel Technology
The most insidious tracking method uses pixels so small they're literally invisible to the human eye. These 1x1 pixel "ghosts" are embedded throughout PDF documents and activate the moment you open the file.
How Ghost Pixels Work:
- Microscopic transparent images scattered in the PDF
- Each pixel connects to a different tracking server
- Your PDF reader automatically loads these "images"
- Servers instantly log your IP, location, and device data
- Multiple pixels create redundant tracking for reliability
Detection Difficulty: Nearly impossible without specialized tools
🎭 Phantom Link Masquerading
What appears to be a simple PDF download is actually a sophisticated tracking operation using phantom links that masquerade as legitimate file URLs.
The Phantom Process:
- URL Spoofing: Links appear to point directly to PDF files
- Invisible Redirects: Multiple server hops collect data
- Cloaking Technology: Different content for bots vs. humans
- Delayed Delivery: PDF served only after data collection
🧬 DNA Document Fingerprinting
The most advanced systems create unique "DNA" for each document copy, making every single PDF traceable back to its specific recipient.
DNA Elements:
- Microscopic variations in text positioning
- Invisible character insertions
- Unique metadata signatures
- Personalized tracking codes in document structure
- Recipient-specific invisible watermarks
🎯 Real-World Surveillance Cases
🕴️ Case Study: The Corporate Leak Hunt
A Fortune 500 company suspected internal document leaks. They embedded invisible tracking in confidential PDFs distributed to different departments:
- Discovery: 47 unique document versions were created
- Tracking: Each version had invisible recipient identifiers
- Revelation: Documents were being accessed from competitor IP addresses
- Investigation: Traced back to specific employees through document DNA
- Outcome: Three employees terminated for corporate espionage
Surveillance Duration: 6 months of invisible monitoring
🎓 Case Study: The Academic Surveillance Network
A major university implemented invisible tracking across all research papers and course materials:
- Scale: 50,000+ documents under surveillance
- Targets: Students, faculty, external researchers
- Data Collected: Reading patterns, collaboration networks, research interests
- Purpose: "Academic performance optimization" and "plagiarism prevention"
- Reality: Comprehensive behavioral profiling of academic community
🔍 The Professional Surveillance Toolkit
🛠️ Industrial-Grade Tracking Platforms
Professional surveillance operations use sophisticated platforms that make tracking completely invisible:
Platform Capabilities:
- Zero-Footprint Tracking: Absolutely no visible indicators
- Real-Time Monitoring: Live surveillance dashboards
- Behavioral Analysis: AI-powered pattern recognition
- Network Mapping: Relationship and influence analysis
- Threat Assessment: Risk scoring based on behavior
⚙️ Advanced Configuration Options
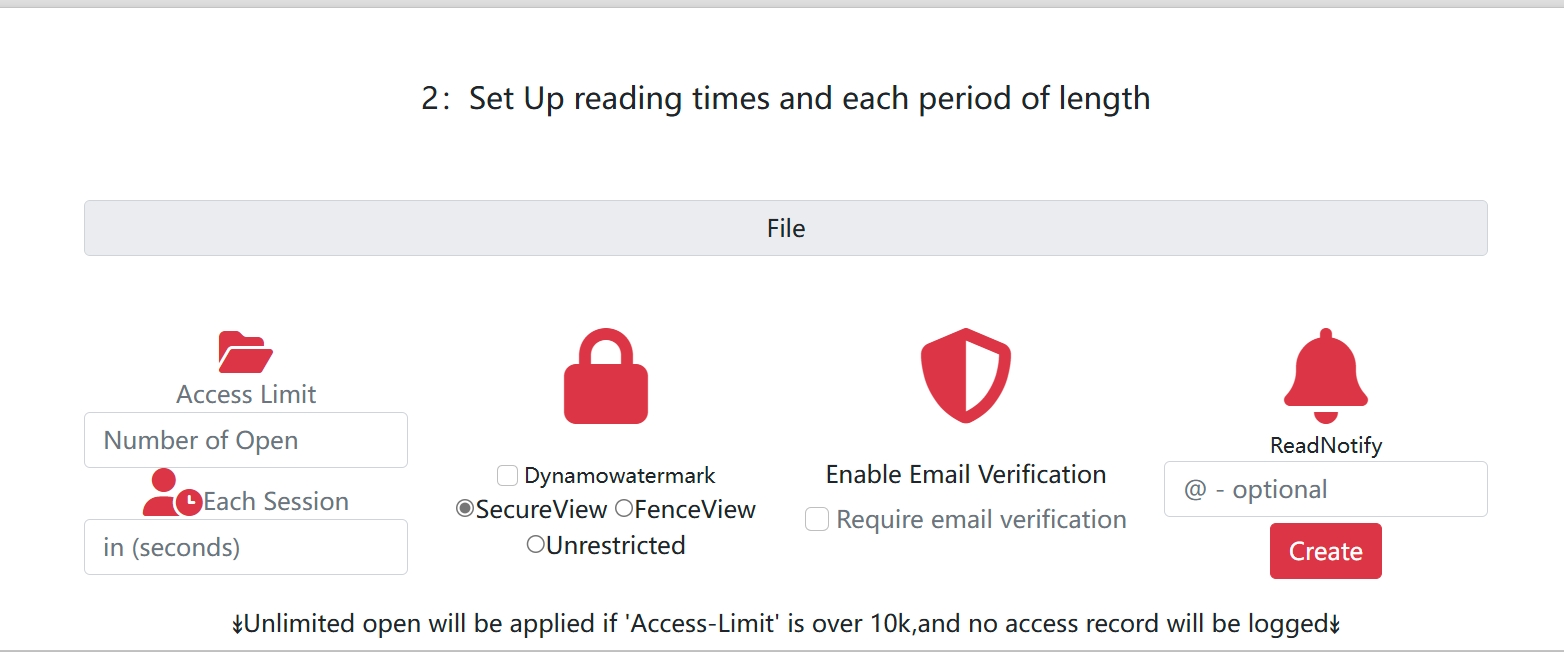
Invisible Surveillance Settings:
- Stealth Mode: Complete invisibility to detection tools
- Multi-Vector Tracking: Multiple simultaneous tracking methods
- Adaptive Evasion: Automatic adjustment to avoid detection
- Deep Packet Inspection: Analysis of network traffic patterns
- Behavioral Triggers: Alerts based on suspicious activity
📊 The Intelligence Goldmine
🧠 Psychological Profiling Through Reading Behavior
Advanced systems don't just track what you do – they analyze why you do it:
- Cognitive Load Analysis: How quickly you process complex information
- Attention Mapping: What captures and holds your focus
- Decision Speed Profiling: How fast you make judgments
- Stress Indicators: Behavioral patterns under pressure
- Influence Susceptibility: How easily you're persuaded
- Risk Tolerance: Your comfort with uncertainty
🌐 Network Intelligence Gathering
- Corporate Network Mapping: Identifying organizational structures
- Personal Relationship Analysis: Who you share information with
- Influence Network Detection: Your role in information spread
- Security Posture Assessment: Your cybersecurity awareness level
- Economic Profiling: Financial status indicators
🚨 Detection and Defense
🔍 How to Detect Invisible Tracking
Professional methods to identify hidden surveillance in PDFs:
Technical Detection:
- Network Traffic Analysis: Monitor all outbound connections
- PDF Structure Examination: Analyze document metadata and embedded objects
- Sandboxed Testing: Open documents in isolated environments
- Reverse Engineering: Deconstruct PDF structure for hidden elements
- Behavioral Analysis: Look for unusual system behavior
Behavioral Indicators:
- Unexpected network activity when opening PDFs
- Slight delays in document loading
- Unusual file sizes for simple documents
- Multiple server connections during viewing
🛡️ Advanced Protection Strategies
- Air-Gapped Systems: Completely isolated networks for sensitive documents
- PDF Sanitization: Strip all potentially malicious elements
- Virtual Machine Isolation: Contain tracking within disposable environments
- Network Segmentation: Limit document access to specific network zones
- Behavioral Obfuscation: Randomize reading patterns to confuse profiling
⚖️ The Legal and Ethical Battlefield
🚨 Legal Gray Areas
- Consent Ambiguity: When is explicit permission required?
- Jurisdiction Shopping: Companies choosing favorable legal environments
- Data Residency: Where surveillance data is stored and processed
- Third-Party Sharing: Who else gets access to collected intelligence
- Retention Periods: How long surveillance data is kept
🌍 Global Surveillance Regulations
- GDPR (EU): Strict consent and disclosure requirements
- CCPA (California): Consumer rights to know and delete
- PIPEDA (Canada): Purpose limitation and minimization
- Lei Geral (Brazil): Data protection and individual rights
- PDPA (Singapore): Consent and notification obligations
🔮 The Future of Invisible Surveillance
🚀 Next-Generation Tracking Technologies
- AI-Powered Behavioral Prediction: Anticipating actions before they happen
- Biometric Integration: Eye tracking and physiological monitoring
- Quantum Encryption Tracking: Unhackable surveillance methods
- Blockchain Audit Trails: Immutable surveillance records
- Neural Network Profiling: Deep learning personality analysis
- Cross-Reality Tracking: Monitoring across physical and digital worlds

💡 The Surveillance Awareness Imperative
🎯 What You Must Understand
- Surveillance is Everywhere: Assume every PDF may be tracking you
- Invisibility is the Goal: The best tracking systems leave no trace
- Data is Valuable: Your behavior patterns are worth money
- Legal Protection is Limited: Laws haven't caught up with technology
- Awareness is Defense: Knowledge is your best protection
🔥 The Uncomfortable Truth
Invisible PDF tracking represents a new frontier in digital surveillance. While the technology can serve legitimate purposes, its potential for abuse is enormous. The line between useful analytics and invasive surveillance is increasingly blurred, and most people have no idea they're being watched.
In a world where every document can be a surveillance device, your awareness is your armor.